CEOs, This is Your Wake-up Call
Live with certainty in an uncertain world. Sign up for the FREE LiveReady bi-monthly newsletter and get the insights and tools to be a protector.
What the UHC murder can teach us about the future of security
The shooting death of UnitedHealthcare CEO Brian Thompson has served as catalyst for two very different reactions. On one side, insurers and many other companies across the US swiftly stripped all pictures of their executives from their websites and increased funding for executive security. On the other side, an increasingly vocal fringe has been openly celebrating Thompson’s murder.
Comrade Workwear, a self-described “socialist clothing company,” went so far as to create a “CEOs Most Wanted” card game, where each playing card in a traditional deck “shines a spotlight on a different titan of greed.” This is a direct parallel to the US military’s practice of using playing cards to familiarize our soldiers with high-profile enemy targets in battle.
The phenomena of idolizing and glorifying assassins, mass killers, and even serial killers is of course nothing new—from women offering to marry Ted Bundy, to Arianna Grande telling a fan that Jeffrey Dahmer is her dream dinner date, to the idolization of mass killers by others who’ve followed in their wake. But Thompson’s murder has given rise to an unprecedented reaction from a sizeable number of people on social media.
A report by NCRI: Network Contagion Research Institute listed the following disturbing facts in the days following the killing:
Out of the top ten most engaged posts on Twitter/X that mention Brian Thompson or UnitedHealthcare, six either expressed explicit or implicit support for the killing or denigrated the victim.
A post referencing the incident on Twitter/X stated, “Are we starting now then?” and garnered over 1.8 million impressions, with highly engaged comments referencing the start of a “class war.”
Other highly engaged posts across multiple social media platforms include statements suggesting other corporate figures “should fear for their own lives.”
This pattern reflects a permissive attitude toward targeted violence, where glorification of violence encourages and enables copycats. What was once generally confined to small subcultures on social media is now being embraced on mainstream platforms, amplifying risk to successful executives in just about any industry.
Make no mistake: this is not just noise. It’s not just a blip in the news cycle. CEOs, take notice. Just as copycat killers spring up in the wake of every mass shooting, you can bet—as predictably as night following day—that there will be others who emulate the UHC killer, or as is usually the case, attempt to one-up him.
Violence Isn’t Random
The first thing we need is a shift in how we think about violence. Most people tend to fall into the belief that violence is random, like a lightning strike, and therefore unpredictable. This helps us shrug off any personal responsibility we may have toward its prevention and response. But violence isn’t random. It is a process, one that is often every bit as observable and predictable as boiling water. The key is to know what to look for, and how to identify the warning signs of danger, specifically the indicators that someone may in fact be targeting you.
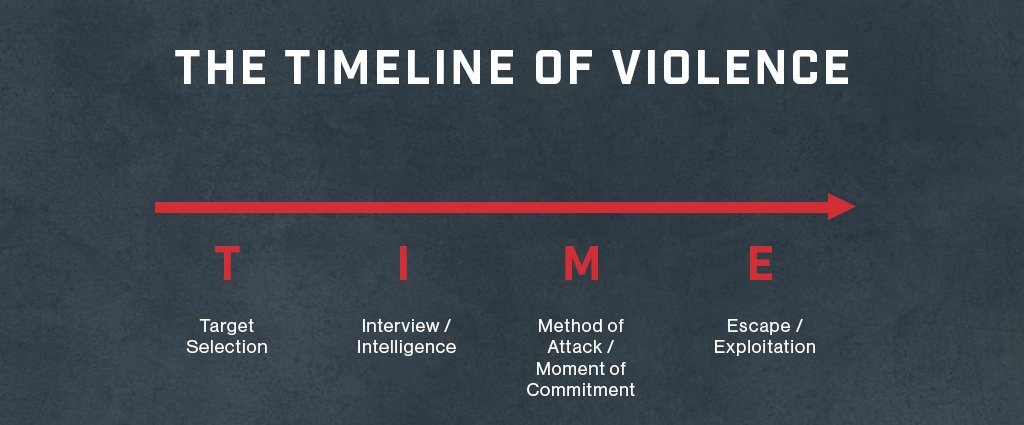
All violent actors, especially those with an ideological mission orientation (assassins, mass killers, and terrorists, for example), follow a discernable pattern of behavior in how they target, plan, and execute an attack. The model I use to outline this pattern is called T.I.M.E.
Target Selection
Intelligence Gathering
Method of Attack
Escape/Exploitation
Regrettably, you can’t always avoid being targeted. No matter how respectfully you treat people or try to avoid trouble, the decision to select you or your organization as a target ultimately lies with the bad guy. This does not mean efforts to avoid trouble, or to treat people decently, are wasted. On the contrary, these efforts can influence and reduce the likelihood of being targeted in the first place. But make no mistake, if someone decides to target you, hoping they won’t carry out an attack is not a strategy, nor is over-reliance on law enforcement to protect you.
If the perpetrator progresses to the point of launching an attack – at the M of TIME – they have chosen the time, place, and method of attack. If you are responding at this point of the process, prevention is out the window, and the best you can hope for is physical defense and damage control.
Knowing you cannot avoid being targeted entirely, and recognizing that you don’t want to be reacting to an attack, the point in the process where you can exert the greatest influence is at the I of TIME.
The I of TIME is where the bad guys’ pre-operational planning takes place. It is where they conduct surveillance, select weapons, and test and probe the target, even to the point of conducting rehearsals of their intended attack. It is also typically where many warning indicators emerge and become visible. Escalating threats, disturbing social media posts or statements, suspicious behavior, etc., may be the result of what the FBI calls “leakage,” where bad guys leak their intent consciously or unconsciously.
Most of the time, these warning signs are readily visible and apparent. The challenge is that threats can emerge from a variety of sources, and organizational leaders – who are often addressing a variety of complex issues on a daily basis, simply don’t know how to spot the fire through the smoke, or where to turn to get good counsel. Many leaders dismiss threats as noise, or delegate the responsibility of threat management to HR partners, corporate counsel, or other members of the leadership team who may not have the experience or skill to do so. Often, the reflexive response is to turn to local law enforcement. But short of the FBI, law enforcement rarely has the resources or expertise to be of real service, nor do they have the mandate to provide you security.
For many decades, being able to properly assess threats or disturbing behavior has been the domain of a highly specialized but little known security specialty called Threat Assessment. The goal of Threat Assessment is to help determine if someone who’s making threats or exhibiting threatening behavior in fact poses a threat, and then based on the dynamics of the case, inform how best to manage the situation to de-escalate and guide security responses.
When a CEO or organization faces threats, without solid guidance from security and Threat Assessment professionals, decision making can feel overwhelming. Trying to find the right balance between real security, expense, and corporate culture can be confusing at best.
But such balance can be achieved. The first step starts by recognizing that you are never helpless in the face of these issues.
You Are Never Helpless
Brian Thompson’s murder should serve as a wakeup call to all organizational leaders. Now is the time to get ahead of the curve, and develop a simple, realistic infrastructure of security to stack the odds in your favor.
As Sun Tzu said in The Art of War: “The art of war teaches us to rely not on the likelihood of the enemy’s not coming, but on our own readiness to receive him; not on the chance of his not attacking, but rather on the fact that we have made our position unassailable.”
So, how do you do it? Here are three actionable steps:
1/ PREPAREDNESS
Preparedness is about taking the rational and logical steps to ensure that you and your organization have the infrastructure in place, in advance, to reduce the likelihood of being targeted in the first place, and to be capable of responding to danger, should it arise.
There are three fundamental actions needed to be prepared:
ASSESS: The first step in managing or improving the preparedness, resiliency, and security of any organization is to thoroughly assess the risks and vulnerabilities associated. Security may be multifaceted and complex, but the solutions are often simple and fundamental.
PLAN: All organizations need to have an emergency response plan (ERP), but all too often, these plans are too complicated or outdated to be of practical value. The industry best-practice approach to Emergency Response Planning is what is called an All-Hazards model. A good All-Hazards ERP provides a simple, vertical approach to communicating and responding to any and all emergencies, including fire, natural disasters, onsite medical emergencies, power and other utilities interruptions, acts of violence, etc. But for ERPs to be effective, they need to be thoughtfully developed, in advance, NOT during the emergency.
TRAIN: All the safety, continuity, and security measures in the world become meaningless if the people they are intended to protect can’t participate in their own protection. This makes training the lynch-pin of most security continuums.
All staff should be trained in the fundamentals of how to spot the warning indicators of potential violence, or I of TIME indicators, as well as what to do in the event of a critical incident, such as an active shooter event.
Managers may receive a higher level of training to better investigate and evaluate threats that arise in the workplace. But executives in today’s world need to invest time to at least understand the fundamentals of threat assessment and management, situational awareness, and personal security, so they are not dependent on outside resources entirely for decision making and their own security.
For both organizations and individuals, the military maxim, “We don’t rise to the occasion, we fall to the level of our training” is true. And like ERP planning, the time to train responses is now – not when you are being targeted.
2/ INTELLIGENCE
As we know, attacks rarely come out of the blue. They are almost always preceded with clear indicators that someone is upset and possibly moving in a dangerous direction. If your team has been trained on what to look for, the likelihood of spotting these indicators, early enough to effect intervention, increases dramatically.
Having the right training in place, along with the right external Threat Assessment counsel to call on, increases your ability to make good, timely decisions about when and how to intervene, or deploy security assets to protect your people, property and profits.
3/ PROTECTION
Most of the time, it is simply not feasible, economically or logistically, to deploy close protection for all executives, all the time. This is why the emphasis on Preparedness and Intelligence should be the priority.
However, should a threat rise to the level where professional lifeguards are needed, it’s essential that those protective services are vetted and available ahead of time.
Security also needs to be deployed, and intelligently. Placing an unarmed security guard in the lobby may feel good, but it could also be functionally meaningless in the face of a motivated attacker. Putting a security guard in a car outside the CEO’s house for some number of days/weeks may be equally meaningless tactically, and often proves more expensive emotionally than financially. The side-effects of fear from children and other vulnerable family members thinking about how someone might be out to get them often makes the “cure” more harmful than the disease.
Protective services are a valuable tool in your toolbox, but when it’s called for, it needs to be executed in a way that is both tactically viable to the threat at hand, and thoughtfully, with a high level of discretion around potential consequences.
It’s good to have lifeguards, but ultimately, it’s better to know how to swim.
In today’s world, it is important to have the right protective assets to call on, should you need, but these are costly tools you rarely want to use.
Like good accounting and legal counsel, it’s advisable to develop the right intelligence assets to assist in evaluating and managing high-risk situations, should they arise, but with the right training, you and your people can handle most of the heavy lifting. You just need to know what to look for, when to look, and how. This way, you only need to bring in expert counsel when the situation demands.
Preparedness, on the other hand, is an investment, one that yields a remarkable return – not just from a security standpoint, but on a daily basis.
Proper assessment and planning lay the foundation for a stronger, more resilient infrastructure, not just for security, but for any emergency. Training anchors a culture of awareness, personal responsibility, confidence, and adaptability into the DNA of an organization—ultimately making you and your organization a far more resilient and harder target, and thereby, far less likely to be targeted in the first place.
Protect your future, yourself, and your people
Your security is not just an expense; it’s an investment in your leadership, your people, and your future. Don’t wait for the next wake-up call—be ready today.
Get started on your own plan:
Read LiveReady: A Guide to Protecting Yourself in an Uncertain World for guidance on conducting your own vulnerability assessment.
Contact us here: Reach out to discuss staff training, vulnerability assessments, or executive training.